RemcosRAT is packed using AutoIT in this case and we will be using x64db to unpack the sample.
Packed Sample – d017b85238bc37936397fca235c6a004b659dda441cfd34cc8d00710e47b0496
We’ll be setting the initial Breakpoints in below calls to detect possible code injection and bypass debugger detection:
VirtualProtect
VirtualAlloc
IsDebuggerPresent
CreateProcessInternalW
IsDebuggerPresent gets hit multiple times and we can bypass it by changing the return output of EAX to 0. VirtualProtect and VirtualAlloc gets hit as well, however it’s not injecting an unpacked executable.
Continuing the analysis, CreateProcessInternalW gets hit and it’s executing startup.bat (from C:\Users\TH7\AppData\Local\Temp\startup.bat) which is dropped by the sample.
Below Image shows the content of startup.bat and we can see that certutil.exe (https://lolbas-project.github.io/lolbas/Binaries/Certutil/) is used to download remcos_agent.exe from hxxp://al-sharqgroup[.]com/remcos_agent[.]exe to Startup folder C:\Users\%username%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\yourfile.exe as yourfile.exe. This is a persistence technique as the sample gets executed during startup.
I didn’t connect my lab to Internet, however we can see from VT that hxxp://al-sharqgroup[.]com/remcos_agent[.]exe downloads Remcos RAT sample e5d56a9880242b2d754c16974f3f35a91b98de9fbaf718360ca64099e13a38bf, did a quick review and observed that this is not a packed sample.
https://www.virustotal.com/gui/url/4aaafea293a0c37ac2a9bc862564d666dbcda484990bb337f162f5ac0b6bc4f2/relations
Continuing the debugging process, we can see that CreateProcessInternalW gets hit again and it’s executing the packed sample we are analyzing (located in desktop as winrar.exe) again.
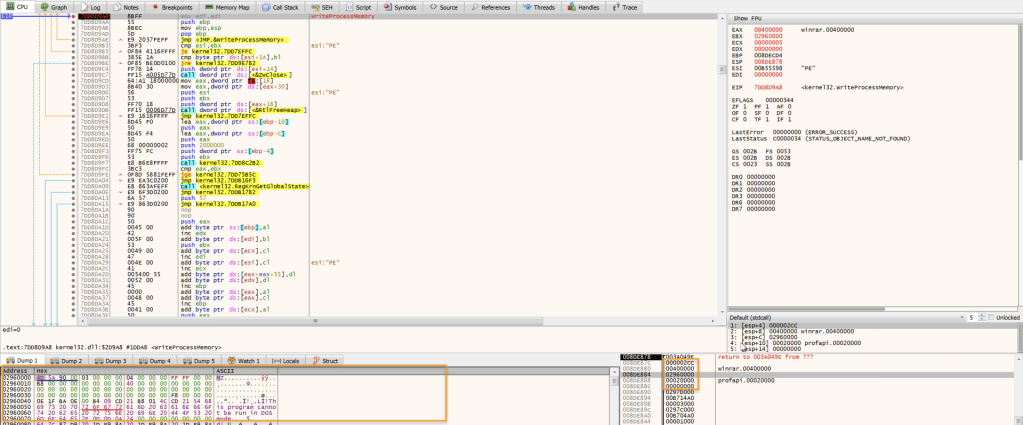
Setting the below breakpoints to continue analysis, WriteProcessMemory can be used to write an executable into the memory of another process and NtResumeThread or CreateRemoteThread can be used to resume the process.
WriteProcessMemory
NtResumeThread
CreateRemoteThread
Continue debugging and WriteProcessMemory gets hit, from the below screenshot we can see that the data is being written to Base Address 00400000 (lpBaseAddress) and 02960000 (lpBuffer) is the data that will be written, following DWORD in dump at 02960000 and we get the unpacked Remcos RAT 5b4ff5b3cfc9395bbd6e5a6f3765ad2ea86be7761b4e18b5dda0fe18fb06e20f (NtResumeThread will resume the process after that).